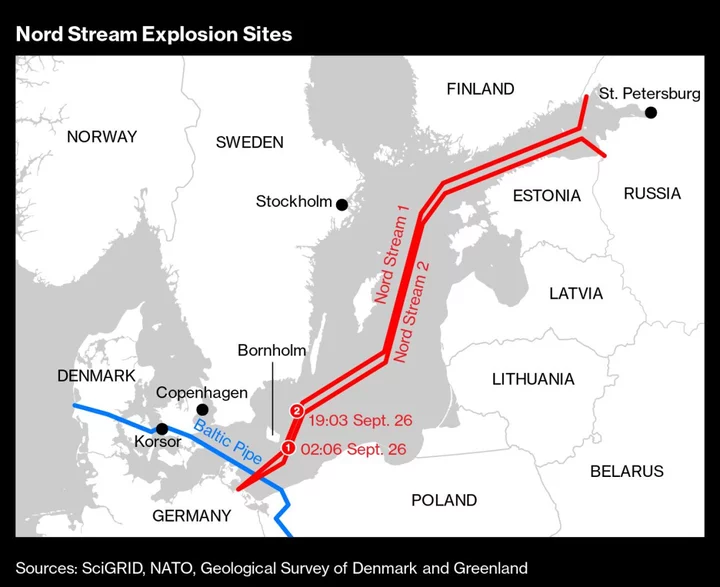
The NATO military alliance is racing to develop technologies to allow real-time detection of suspicious activity near underwater critical infrastructure, after the Nord Stream pipeline blasts one year ago laid bare the difficulty of monitoring.
Fourteen nations from the alliance, along with Sweden, are testing sea drones, sensors and the use of AI in a 12-day exercise off the coast of Portugal that ends Friday. The exercise comes as Russia continues to map allied cables and pipelines as possible future targets, according to the North Atlantic Treaty Organization.
NATO has yet to formally accuse any actor for the Nord Stream pipeline explosions, highlighting the challenge both governments and private companies face in attributing such attacks.
Real-time detection “sends a deterrence signal to the enemy, be it Russia or somebody else,” said Lieutenant General Hans-Werner Wiermann, head of NATO’s cell for protecting undersea infrastructure.
If bad activity can be detected, that allows the 31 NATO allies to consider diplomatic or military responses based on a “firm foundation of information,” he told reporters visiting the exercise in Troia, south of Lisbon. The aim is to spot malicious behavior around underwater infrastructure as it happens, and to share that information with governments and private operators.
Russia has denied early accusations from some western nations it was responsible for the Nord Stream blasts. But incidents in recent months of what appear to be Russian spy ships operating near allied systems have heightened concern, especially in light of Russia’s advanced sub-sea capabilities. These remain largely intact compared to Moscow’s land forces bogged down in its invasion of Ukraine.
NATO warned in May of a significant risk that Moscow could target infrastructure in Europe and North America, particularly to gain leverage against nations helping Ukraine. Moscow is using a combination of its navy warships, scientific ships as well as commercial fishing trawlers, container ships and tankers to trace NATO allies’ critical undersea systems, Wiermann said.
Undersea data cables carry about $10 trillion worth of financial transactions every day and about 95% of global internet traffic, NATO says. Two thirds of the world’s oil and gas is either extracted at sea or transported by sea. Some of the systems are thousands of kilometers long and hundreds of meters deep below the sea, which makes monitoring complex.
In one of the NATO exercises, allies sought to stop a hostile actor attempting to disrupt data networks and wreak havoc on financial markets using a state-sponsored commercial vessel to make their activity more difficult to detect.
Commercial fiber optic sensors on the infrastructure cables detected that the fictitious enemy’s ship was trying to deploy an unmanned underwater vehicle. That information was relayed to NATO’s command and control chain. After confirming the threat, NATO then sent in a combination of aerial, surface and underwater drones to intercept and escort the suspicious vessel.
Technology will play an increasingly important role to prevent that activity in real life. AI can be used to follow the movements of ships and flag if they are crossing over critical infrastructure multiple times, Wiermann said. In future, fiber optic cables themselves may be able to detect meddling nearby.
Highlighting the increasing importance of subsea security, NATO allies agreed in July to establish a new maritime center for undersea critical infrastructure at its maritime command in Northwood, UK. They also agreed to set up a network to improve information sharing between NATO, its allies and the private sector, to act fast on intelligence like the kind picked up by the sensors or AI systems.
After the Nord Stream explosions, most pipeline operators were “very nervous” and launched full scale scans of their assets, monitoring about 9,000 kilometers (5,592 miles) of pipelines, Wiermann said.
“They did it, but it cost them a fortune. And they don’t want to do this necessarily again,” Wiermann said. “We want to have the speediest information exchange between the actors as possible because if we want to detect suspicious behavior in real time, we have to act very quickly.”